Using beneficial ownership data for national security
Overview
National security is a broad concept which has evolved as the ability of a state to protect and defend its citizens to include its society’s norms, rules, institutions, and values more broadly.[1], [a] There has been an increasing focus on how anonymously owned companies can create a threat to national security, and therefore how transparency and visibility of the individuals who ultimately own and control companies – the beneficial owners – can help protect it. There is a range of ways in which a lack of visibility on company ownership can help malign actors circumvent domestic legislation and create loopholes that present security threats, ranging from physical security threats to citizens (e.g. crime and terrorism) to interference with governance (e.g. political corruption, and undermining democracy and the rule of law).
In December 2020, the United States (US) committed to the implementation of a central – albeit non-public – beneficial ownership (BO) register. The main stated reason for the US commitment has been to protect national security.[2] In June 2021, President Biden published a memorandum in which he listed the reporting of beneficial owners and the reduction of offshore financial secrecy as solutions to “countering corruption as a core United States national security interest.”[3] The idea that anonymously owned companies can present security threats has also gained attention through the focus on the influence of foreign funding on domestic politics, such as in Australia[4] and in the European Union (EU).[5] Despite the rhetoric of beneficial ownership transparency (BOT) in the national security context, there is little detailed examination of its role.
Over a hundred jurisdictions have committed to the implementation of BOT reforms, which aim to make information about beneficial owners available to a range of actors who use the data to achieve certain policy goals.[6] BOT, and the use of BO data more broadly, can be used to further numerous policy aims. As the use of BO data emerged in anti-money laundering (AML), its roots are, arguably, in the field of national security.
The US and other countries started implementing AML policies in earnest from the 1970s in response to the drug trade, at a time when the Soviet Union actively encouraged narcotics trafficking by its non-state proxies.[7] The body of AML policies expanded to incorporate countering the financing of terrorism (CFT) during the 1990s, and CFT policies were widely adopted following the 11 September 2001 terrorist attacks.[8] More recently, BOT has proven useful in a range of other policy areas, including: domestic resource mobilisation (e.g. by preventing tax evasion and in assessing the feasibility and enforcement of a wealth tax[9]); public procurement;[10] improving the ease of doing business (e.g. by helping companies better manage risk and leveling the playing field);[11] and resource governance (e.g. in the extractives industry).[12] A comprehensive review of how these policy areas may intersect with the subject of national security and how BOT, specifically, can further national security policy aims has not been conducted.
This briefing sets out how BOT can contribute to specific national security aims across different policy areas. It will focus specifically on the nation state, and on how the implementation of BOT domestically can help further national security aims. The activities of a foreign state or actor in a third country, the perceived threats they may pose, and the ways in which the implementation of BOT in third countries can mitigate these threats are outside the scope of this briefing. In other words, the briefing will not consider potential national security threats to Country A caused by Country B’s activities in Country C, for a few reasons. First, these perceived threats might be more geopolitical in nature and difficult to substantiate, delineate, and define. Second, BOT is most often implemented through a series of reforms at the national level (i.e. Country A does not regulate company ownership transparency in Country C), so is beyond the scope of their action. Third, Country C might welcome Country B’s activities, as can be argued, for instance, in many countries involved in the Belt and Road Initiative.[b]
The briefing will illustrate key BOT use cases for national security using country examples from across the globe. Due to the US focus on this issue, many of the case studies in this briefing will look at the US. The briefing concludes that BOT can help mitigate a range of national security threats, and focuses on five areas. It will start with the policy areas where BOT has its roots. These subjects are already well covered, but the specific added value of BO data in the context of national security is less so:
- preventing corruption and organised crime;
- countering the financing of terrorism;
- enforcing economic and financial sanctions on individuals, organisations, and jurisdictions.
Subsequently, the briefing will look at more recent national security use cases of BOT:
- protecting strategic sectors;
- preventing interference in governance systems and the rule of law.
These issues can have both a direct and indirect bearing on national security. The policy areas are interlinked, but the nature of the security threats, and the ways in which anonymous companies exploit loopholes that BOT can help close, are different. In certain cases, companies can be used to effectively make a country complicit in illegal activities outside its jurisdiction, which can negatively impact national security. In other cases, companies are used to circumvent domestic laws which are in place to safeguard national security interests (e.g. political lobbying regulations). A number of these relate to corruption, whilst others relate to fraud or the enforceability of established legislation. In all cases, corporate structures are used to hide the true identity of those who actually own and control companies.
The threats can involve both state and non-state actors. It is often difficult to determine whether activities that pose potential security threats emanate from state or non-state actors, and where the difference is unclear (e.g. with state-owned or state-linked companies, or with state-owned or politically linked companies). Anonymous companies can be used by both state and non-state actors as an intentional tactic to exploit security weaknesses in a country. Other times the intent can be different (e.g. self-enrichment), but the action can nevertheless be damaging to national security. The term strategic corruption describes cases where actions are coordinated by a hostile state and there is clear intent to undermine national security.[c] The actions themselves may involve non-state actors, with or without their knowledge. The use of anonymously owned corporate structures makes it very hard to know if a state actor is involved. In strategic corruption, corrupt inducements are wielded against a target country by foreigners as a part of their own country’s national strategy.[13]
National security cuts across a range of policy areas, and, therefore, BO information will need to be made available to a range of different actors to effectively counter security threats. BOT and the presence of BO data alone will not achieve policy outcomes. Impact requires the data to be usable and used, and may need complementary legislation which the data can help monitor and enforce. The main value of BO data is its use in combination with other relevant data (e.g. procurement data), meaning structured and interoperable data is most effective. Foreign state ownership of companies is relevant and should therefore be captured as part of BO disclosures in a standardised way.[14] To achieve its aim, central and public BO registers provide the most effective access to the broadest range of different actors.[d] Beyond specific use cases, BOT provides visibility and knowledge of who is operating in an economy and financial system, which is fundamental information for knowing how best to protect it.
Figure 1. How beneficial ownership information can be used for national security
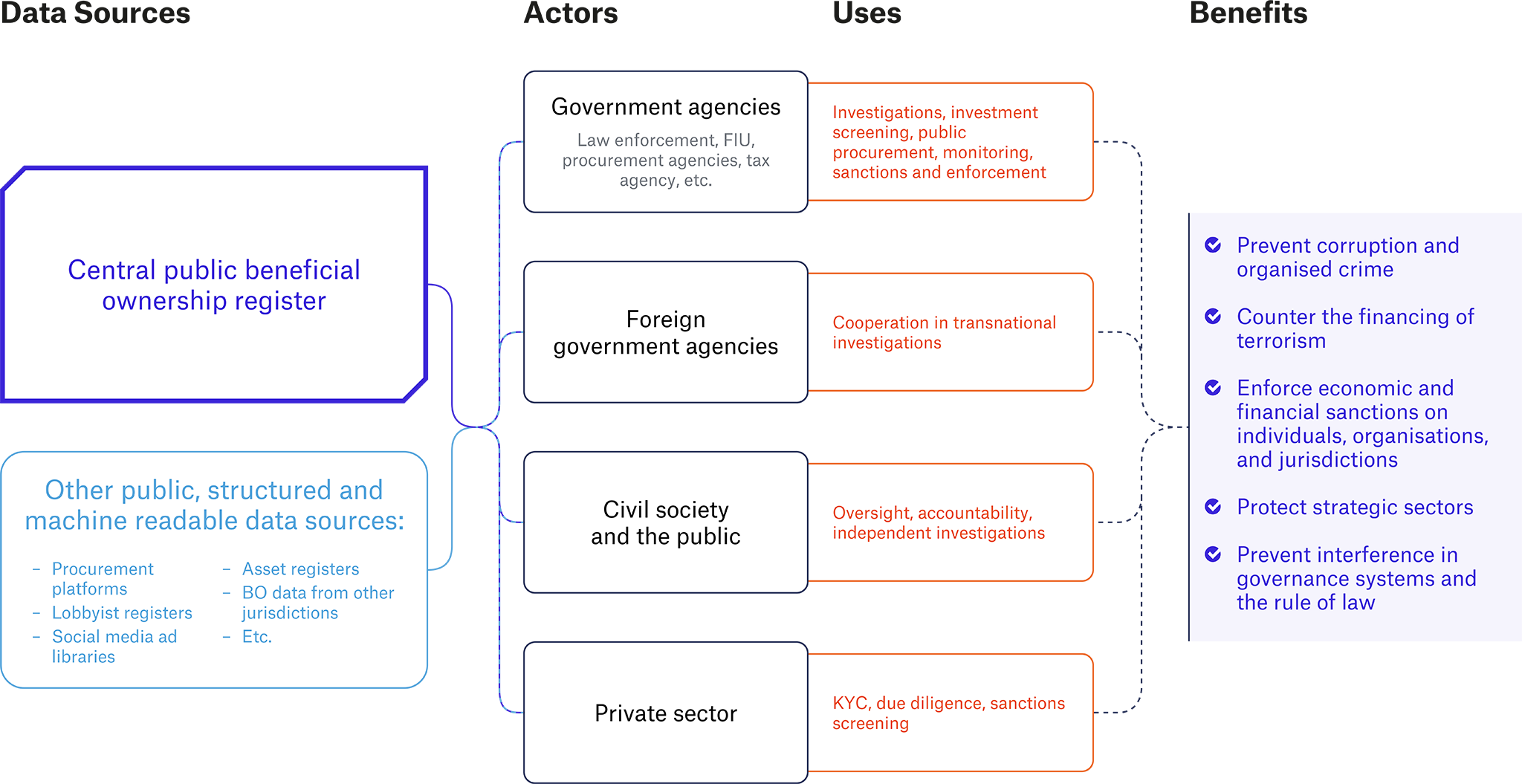
The diagram visualises the flow of BO information and complementary data to actors that can contribute to safeguarding national security. Governments can collect and verify BO information in central registers for all companies in an economy as part of commitments or international obligations. Central registers are the most effective way to provide access for authorities. Making the information public means the data is available to the widest possible set of actors, and can decrease access times for certain data users, such as foreign law enforcement. Structured data is more easily integrated with other data sources and improves overall usability.
BO information can be used by actors in a range of different ways to strengthen a range of national security outcomes, including by using data in investigations and due diligence, monitoring, sanctioning and enforcing legislation, and to screen investments and improve public procurement. This helps prevent corruption and organised crime; counter the financing of terrorism; enforce economic and financial sanctions on individuals, organisations, and jurisdictions; protect strategic sectors; and prevent interference in governance systems and the rule of law.
Footnotes
[a] For example, New Zealand includes protecting the country’s “status as a free and democratic society from unlawful acts or foreign interference” in its national security definition. At China’s National Security Commission’s first meeting on 15 April 2014, President Xi Jinping articulated the concept of ‘holistic’ or ‘overall national security’ (Zongti guojia anquanguan), comprising 11 areas of concern, including political security, which has also been institutional security or ideological security. See: “Defining National Security: The agencies’ role in protecting New Zealand”, Department of the Prime Minister and Cabinet, September 2017, https://dpmc.govt.nz/sites/default/files/2017-09/fact-sheet-3-defining-national-security_1.pdf; Shen Dingli, “Framing China’s National Security”, China US Focus (blog), 23 April 2014, https://www.chinausfocus.com/peace-security/framing-chinas-national-security/.
[b] The Belt and Road Initiative is a major Chinese global infrastructure development strategy, adopted in 2013, that seeks to connect Asia with Africa and Europe via land and maritime networks through significant infrastructure investments. Around 140 countries have signed up to the initiative. It is considered part of China’s growing efforts to exert influence which is seen by some other countries as a threat. See: Wendy Leutert and Jack Nolan, “Signing up or standing aside: Disaggregating participation in China’s Belt and Road Initiative”, Brookings, October 2020, https://www.brookings.edu/articles/signing-up-or-standing-aside-disaggregating-participation-in-chinas-belt-and-road-initiative/.
[c] Also known as weaponised corruption.
[d] Kiepe, “Making central beneficial ownership registers public”. These and other best practices for effective beneficial ownership disclosure are detailed in the Open Ownership Principles. Effective disclosure generates actionable and usable data across the widest range of policy applications, and minimises loopholes. See: “Principles for Effective Beneficial Ownership Disclosure”, OO, July 2021, https://www.openownership.org/principles/.
Endnotes
[1] See, for example: “9-90.010 - National Security”, US Department of Justice, n.d., https://www.justice.gov/jm/jm-9-90000-national-security#9-90.010; Tang Aijun, “Ideological Security in the Framework of the Overall National Security Outlook”, Central Party School of the Chinese Communist Party, Socialism, No. 5 (May 2019), http://socialismstudies.ccnu.edu.cn/bencandy.php?fid=71&id=1985; “The National Security Strategy of the United Kingdom”, UK Cabinet Office, March 2008, 3-4, https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/228539/7291.pdf; Samuel M. Makinda, “Sovereignty and Global Security”, Security Dialogue 29, no. 3, September 1998, 281-292; Jude Blanchette, “Ideological Security as National Security”, Center for Strategic and International Studies, 2 December 2020, https://www.csis.org/analysis/ideological-security-national-security.
[2] Joseph R. Biden Jr., “Memorandum on Establishing the Fight Against Corruption as a Core United States National Security Interest”, The White House, 3 June 2021, https://www.whitehouse.gov/briefing-room/presidential-actions/2021/06/03/memorandum-on-establishing-the-fight-against-corruption-as-a-core-united-states-national-security-interest/.
[3] Ibid.
[4] “Second interim report on the inquiry into the conduct of the 2016 federal election: Foreign Donations”, Commonwealth of Australia, March 2017, https://www.aph.gov.au/Parliamentary_Business/Committees/Joint/Electoral_Matters/2016Election/Report_1.
[5] Ieva Dunčikaitė, Jorge Valladares, and Deimantė Žemgulytė, “Paying for Views: Solving transparency and accountability risks in online political advertising”, TI, 2021, https://images.transparencycdn.org/images/2021_Report_PayingForViews-OnlinePoliticalAdvertising_English.pdf.
[6] In all these instances, there are additional benefits that arise from making central registers available to the public. See: Tymon Kiepe, “Making central beneficial ownership registers public”, May 2021, OO, https://www.openownership.org/resources/making-central-beneficial-ownership-registers-public/; “Worldwide commitments and action”, Open Ownership, n.d., https://www.openownership.org/map/.
[7] Ian Michael Oxnevad, Making a Killing: States, Banks, and Terrorism (Montreal: McGill-Queen’s Press, 2021), 16.
[8] Ibid, 17.
[9] Arun Advani, Emma Chamberlain, and Andy Summers, “A wealth tax for the UK”, Wealth Tax Commission, 2020, https://www.wealthandpolicy.com/ wp/WealthTaxFinalReport.pdf.
[10] Tymon Kiepe and Eva Okunbor, “Beneficial ownership data in procurement”, OO, March 2021, https://www.openownership.org/resources/beneficial-ownership-data-in-procurement/.
[11] Tymon Kiepe and Sadaf Lakhani, “The use of beneficial ownership data by private entities”, OO, forthcoming.
[12] “Disclosing beneficial ownership”, EITI, May 2017, https://eiti.org/files/documents/eiti_bo_factsheet_en_final.pdf.
[13] Eric Edelman, Kristofer Harrison, Celeste Ward Gventer, and Philip Zelikow, “The Rise of Strategic Corruption: How States Weaponize Graft”, Foreign Affairs, July/August 2020, https://www.foreignaffairs.com/articles/united-states/2020-06-09/rise-strategic-corruption.
[14] “The Open Ownership Principles – Sufficient detail”; Jack Lord, “State-owned enterprises and beneficial ownership disclosures”, OO, October 2021, https://www.openownership.org/blogs/state-owned-enterprises-and-beneficial-ownership-disclosures/.